How to Use Chattr Command in Linux (for Beginners)
Chattr is a UNIX command-line program that’s pre-shipped in most Linux distributions. The role of this command is to allow the admin user to set file attributes that impose restrictions on files.
There are a handful of file attributes for different roles, such as the “+i” attribute, which prevents a file from being renamed, deleted, or modified, and the “+a” attribute, which only allows appending new content, as well as a few others that will be discussed later in this tutorial.
The benefit of using this command is that the restriction applies to both the normal user and the root user, making it a good choice for protecting important and sensitive files from accidental or retroactive changes.
In this beginner-friendly tutorial, I’ll explain to you how to use the chattr command with its various options, operators, and file attributes in a real-world scenario.
Tutorial Details
| Description | Chattr command |
| Difficulty Level | Low |
| Root or Sudo Privileges | Yes |
| OS Compatibility | Ubuntu, Manjaro, Fedora, etc. |
| Prerequisites | – |
| Internet Required | No |
Syntax of the Chattr Command
The chattr command takes three arguments: the first is the option, the second is the file attribute, and the third is the file path where you want to apply the selected file attribute.
$ chattr [option] [attribute*] [path/to/file*]When you specify the file attribute, you’ll mainly use the “+” and “-” operators: the “+” operator adds the selected attribute restriction to the file, while the “-” operator removes it. Besides this, you use the “=” operator to remove all the existing attributes and replace them with the selected ones.
The available options for chattr are the “-R” option to recursively apply the specified attribute to every file in the selected directory, the “-V” option to display the changed files, and the “-f” option to hide common errors.
Enjoying it, right? Now, let’s learn a bit more about some important file attributes that you’ll mainly use for setting restrictions using the chattr command, starting with…
List of File Attributes for Chattr Command
The following is a list of commonly used chattr attributes and their purposes.
a: Only allow appending new content while imposing write, rename, and delete restrictions.A: Access time (or atime) record is frozen.c: Enables the transparent compression of the file on the supported filesystem.S: The changes to the file are updated synchronously, which will ensure the integrity of the critical data.i: Enables immutable mode, which allows the file content to be viewed but prevents writing, renaming, deleting, or appending actions.j: It will ensure that the changes are first applied to the ext3 journal before the file itself.t: Disable the tail-merging.d: It will reject the dump process for the selected file, which is often used for creating backups.u: When a file is accidentally deleted, a copy of the file is generated and can be recovered later.e: It’s a default attribute applied to all files that indicates the file system uses extents to map the file’s location on the disk.
The above list contains a few attributes from the complete list. To see the entire list, you can use the “man chattr” command. However, these are sufficient for a beginner, as your work will mostly revolve around them. Let’s now look at some practical examples of this attribute in use.
Apply Write, Rename, and Delete Restriction to File
The “+i” attribute makes the file immutable, preventing any modifications, even by root. A real-life scenario would be protecting a critical configuration file from accidental changes.
$ sudo chattr +i myfile.txtOutput:
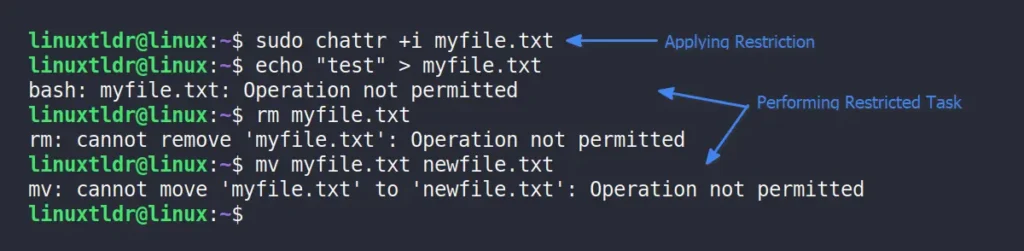
The content of the file can still be viewed despite the write, rename, and delete restrictions.
Remove Write, Rename, and Delete Restriction to File
To remove the restrictions placed on a file in the previous method, you can use the “-i” attribute.
$ sudo chattr -i myfile.txtOutput:
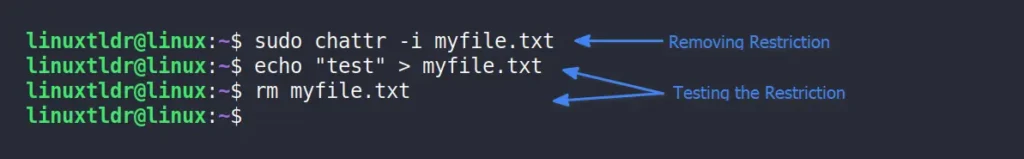
Note that this will only remove the restriction for the “+i” attribute. If the user assigns a different attribute or multiple attributes at the same time, they will still exist.
Apply Append-Only Permission
The “+a” attribute is very similar to the “+i” attribute and prevents write, rename, and delete actions but allows appending new content to the file. You can apply this attribute to log files to prevent retroactive changes.
$ sudo chattr +i myfile.txtOutput:
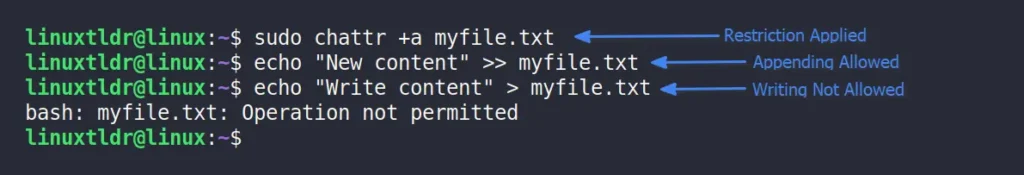
To restore the file to its original state, use the “-a” attribute to remove the append-only restriction.
Check the Applied Attribute to Selected File
To keep track of existing attributes or verify whether the applied attribute is set, you can use the “lsattr” command, which lists all the attributes assigned to the selected file.
$ lsattr myfile.txtOutput:
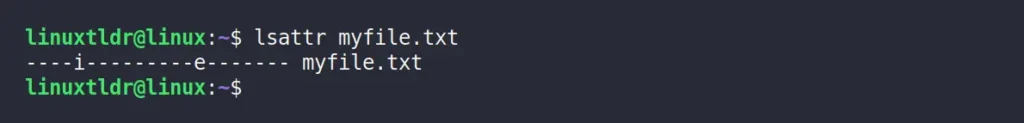
The above output indicates that the file has two attributes: “i“, which means the file is immutable, and “e“, which is the default attribute applied to all files.
Replace the Existing Attribute With New Attribute
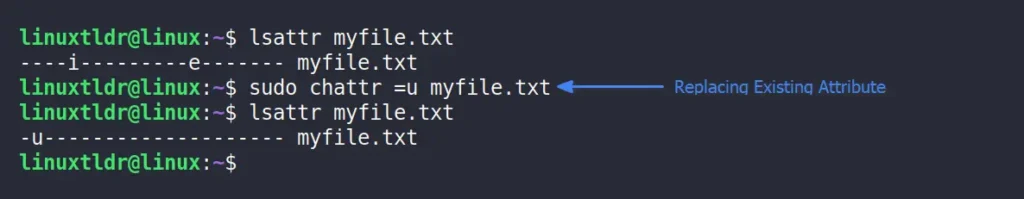
When a file has multiple attributes applied to it but you want to replace all of them with the selected one, you can specify the attribute with the “=” operator for this task.
$ sudo chattr =u myfile.txtOutput:
Apply the Attribute to All Files Within the Selected Directory
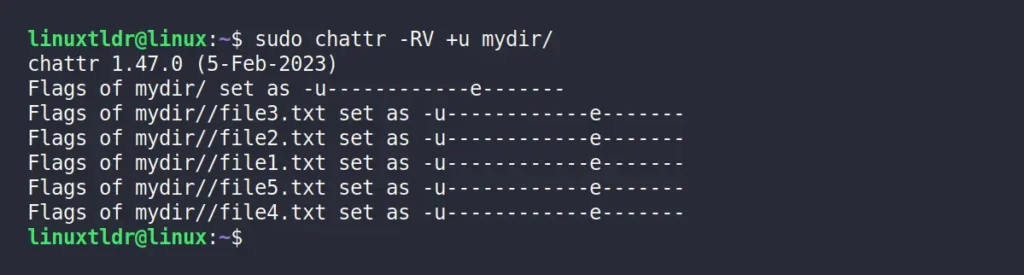
To apply a selected attribute to all files in the target directory, use the “-RV” option to make changes recursively to all files, and then list the affected files.
$ sudo chattr -RV +u mydir/Output:
Wrap Up
In this article, you have learned how to use the chattr command with various operators and attributes, as well as its available options. If you have any questions about the topic, feel free to reach out to us via the comment section.
Till then, peace!
The post How to Use Chattr Command in Linux (for Beginners) appeared first on Linux TLDR.